Viewing an Incident
Go to Email Security > Incidents. Incidents reported by a user are listed in the Action Needed tab. In the Resolved tab, you can see incidents flagged by the system, including auto remediation if you've set that up, and the ones you've marked as safe or sent to junk (remediated).
You can manage how the table is displayed as follows:
Use the Search
 box to search the list of incidents.
box to search the list of incidents.Select the column
 icon to manage how table columns are displayed. By default, all columns are visible and arranged in a specific order. You can change the display by doing the following:
icon to manage how table columns are displayed. By default, all columns are visible and arranged in a specific order. You can change the display by doing the following:View or hide columns using the toggle.
Use the reordering
 icon to move columns up and down the list. This changes the left-to-right display. An item at the top of the list, for example, means that it will be the first column on the left. Select Restore Defaults to restore the columns to their default positions.
icon to move columns up and down the list. This changes the left-to-right display. An item at the top of the list, for example, means that it will be the first column on the left. Select Restore Defaults to restore the columns to their default positions.
Resize columns by hovering your cursor over the column boundary you want to adjust until it becomes a resize
 cursor. Drag the boundary until the column is the width you want.
cursor. Drag the boundary until the column is the width you want.Select the up/down
 arrows in the column headers to sort column content.
arrows in the column headers to sort column content.
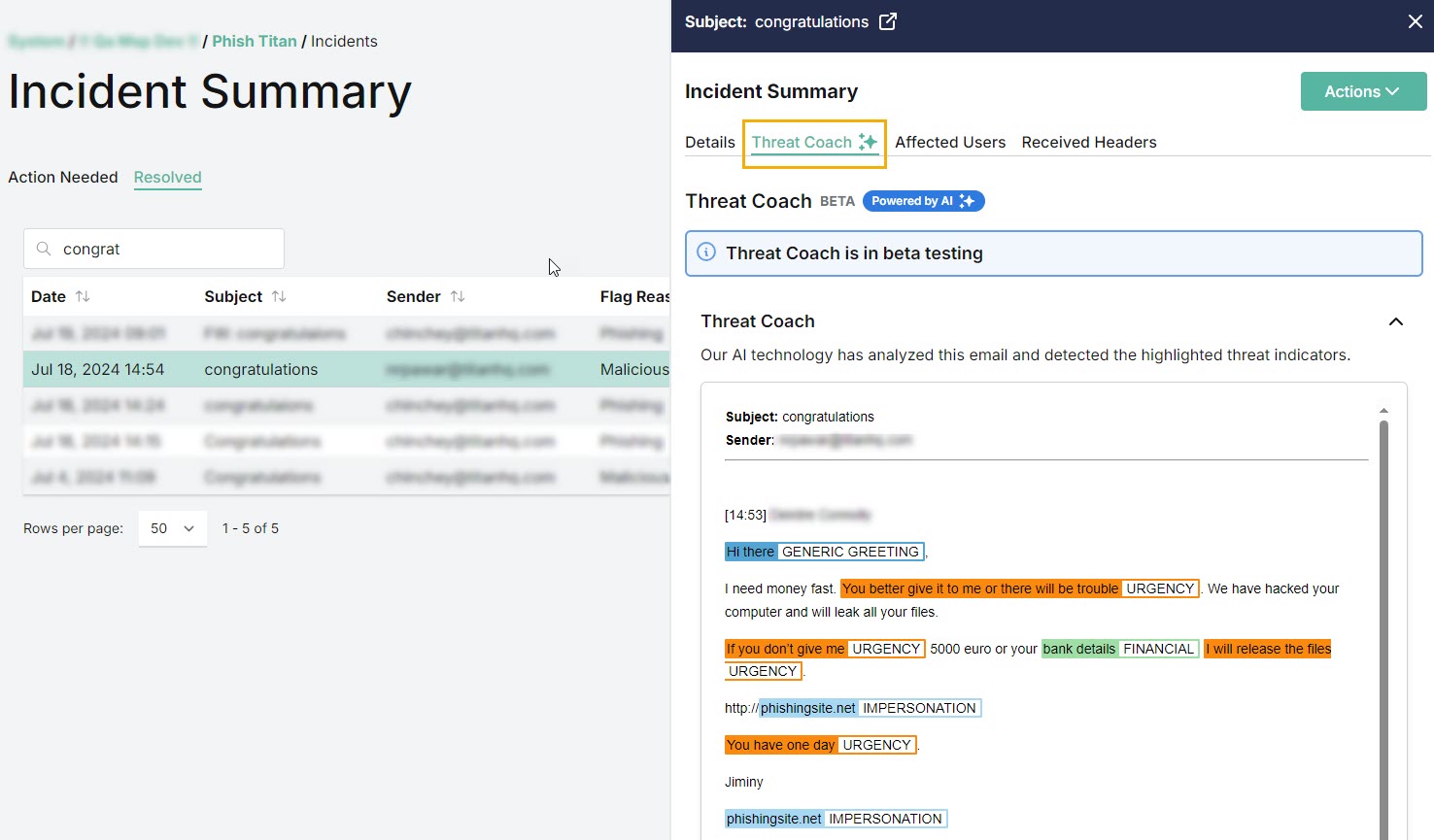
To view additional details of an incident, locate the incident in the table and select it. The Incident Summary slides out from the right side of the page.
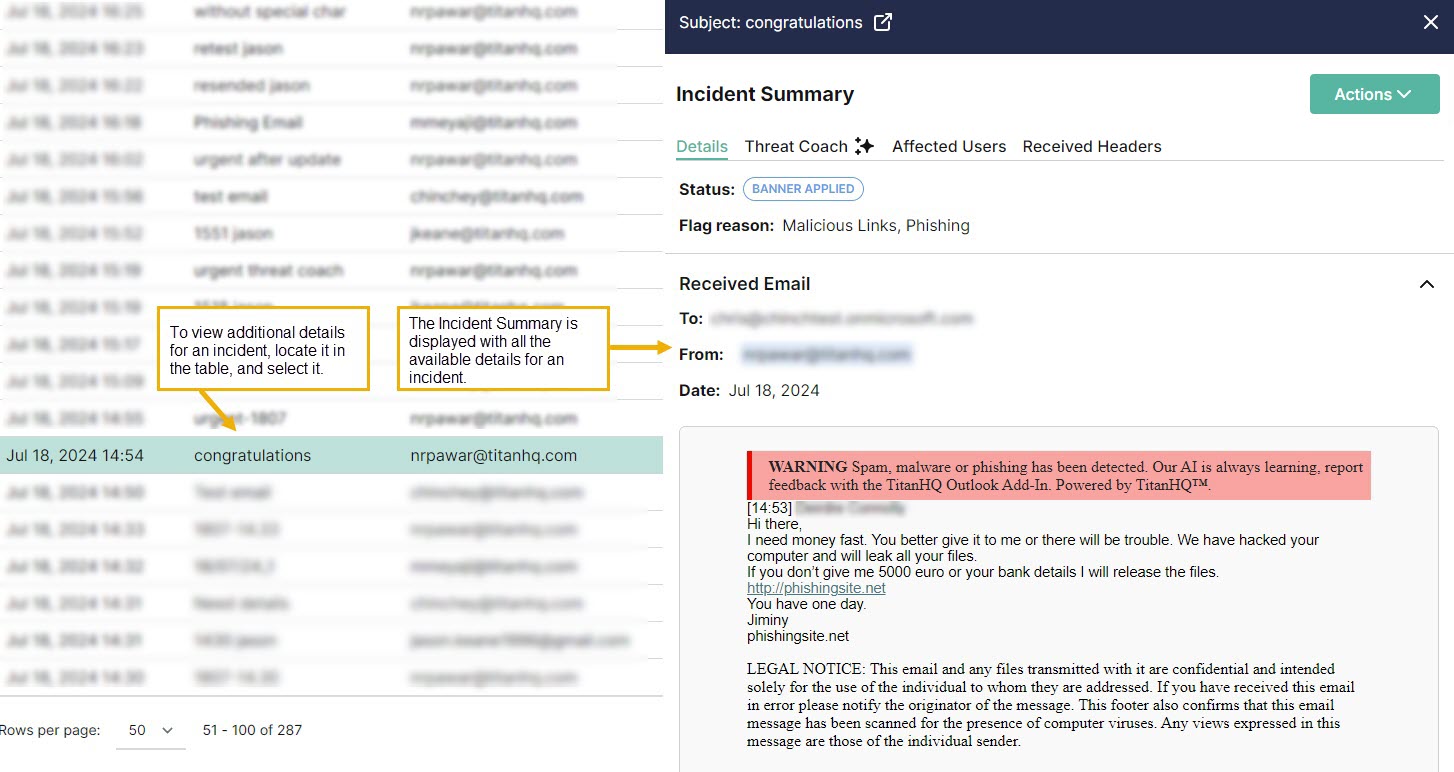
You can move between incidents in the table, and as you select each one, the Incident Summary slideout repopulates with the data. Select the fullscreen
 icon if you want to view the Incident Summary in fullscreen.
icon if you want to view the Incident Summary in fullscreen.Note
If you're a read-only admin, then you don't have access to view the content in the body of this email.
Incident Summary
The Incident Summary page shows all available details for an incident listed in Email Security > Incidents. When you select the incident you want to view in the Incidents table, the Incident Summary page appears as a slideout. You can move between incidents in the table and the Incident Summary page repopulates with the new data. You can select the fullscreen  icon beside the Subject at the top of the page to expand it.
icon beside the Subject at the top of the page to expand it.
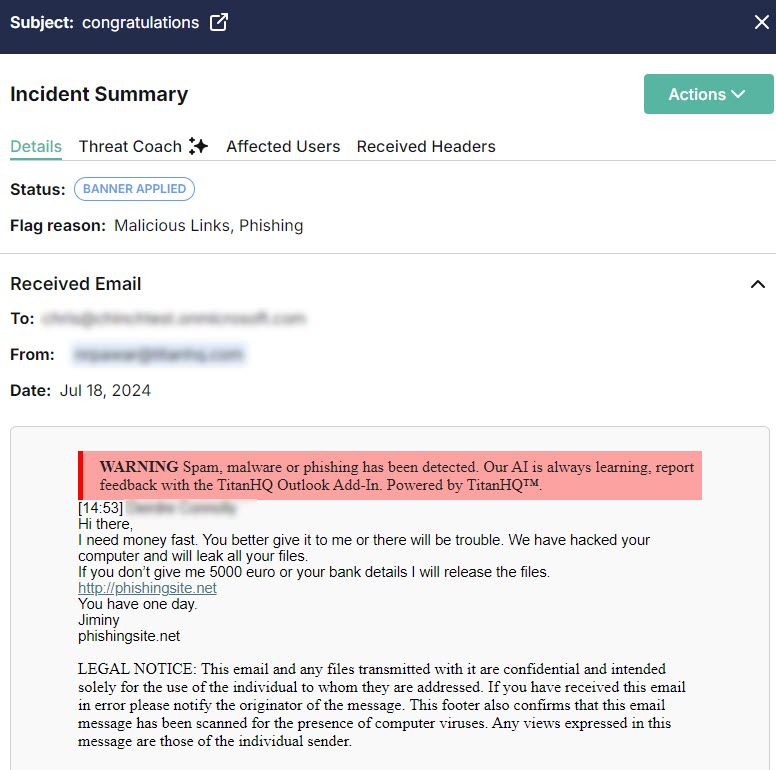
You can navigate the four tabs at the top to find more information about the incident.

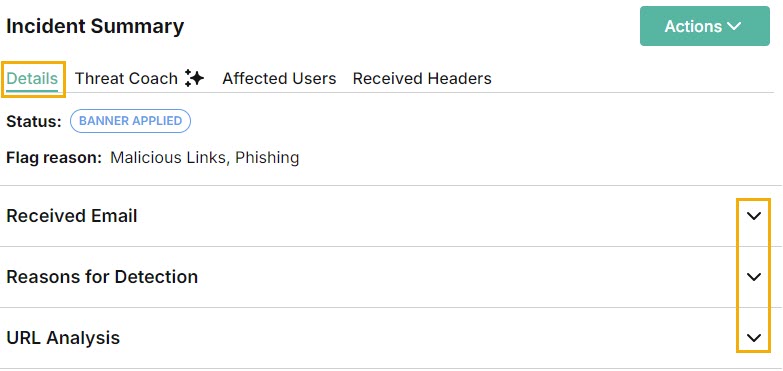
DETAILS
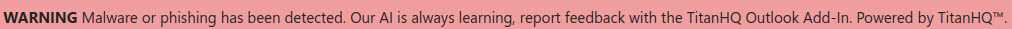
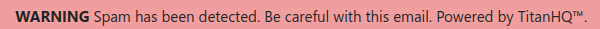
The Details tab is automatically displayed when the Incident Summary page opens. It includes the status, flag reason and content of the email. If the email was flagged as phishing or fraud, Reasons for Detection and URL Analysis sections appear below the Received Email section. All of these sections can be expanded and collapsed by selecting the up/down arrow.
Status
Every incident is assigned a status
Flag Reason
The following table explains reasons why an email can be flagged for further investigation.
Flag Reason
Description
User Reported Phishing
A user reported this email as phishing with the TitanHQ for Outlook add-in.
User Reported Spam
A user reported this email as spam with the TitanHQ for Outlook add-in.
User Reported Clean
A user reported this email as clean with the TitanHQ for Outlook add-in.
Suspicious Text
Email Security detected suspicious text in the body of this email.
Malicious Links
Email Security detected malicious links in the body of this email. A malicious URL is a link embedded in an email that was created with the purpose of promoting scams, attacks, and frauds. When selected, malicious URLs can download ransomware, or lead to phishing or spearphishing emails.
Phishing
Email Security flagged this email as a phishing attempt. Phishing emails attempt to trick people into revealing personal or confidential information which can then be used illicitly; for example, to steal a recipient's money or identity.
Spoofed Display Name
Email Security detected a spoofed display name. Email spoofing is the creation of an email with a forged sender address to intentionally mislead a recipient about its origin.
Spam
Email Security flagged this email as spam. Spam refers to unsolicited emails that are sent to a large number of recipients, usually as advertising.
Fraud
Email Security flagged this email as fraud. Email fraud intentionally deceives the recipient into sharing personal data, such as bank or credit card details.
Graymail
Email Security flagged this email as Graymail. Graymail refers to solicited marketing emails and comes from a legitimate source. Recipients once subscribed to them and now may no longer open or read them.
Exploited Domains
Email Security detected this email as coming from a free email service, which malicious actors frequently use to launch phishing attacks. An alert banner was added as a reminder to users to stay vigilant, even if the email content does not look suspicious.
Actions
From the Actions menu, select an action to take on this incident.
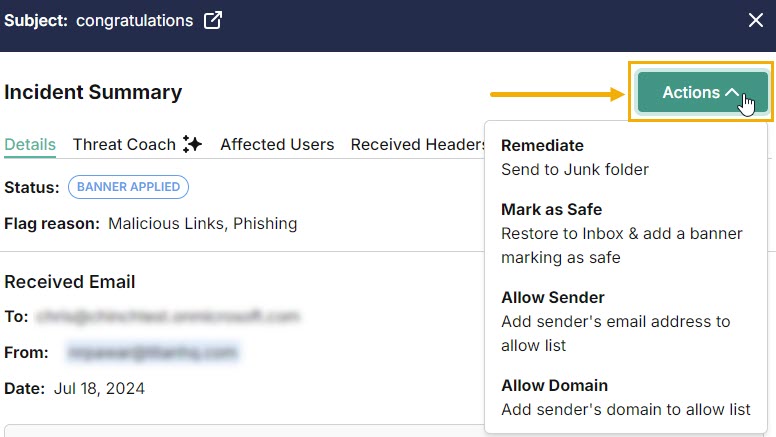
When you select one of the following actions for an email or domain, it is applied to all affected users. Select the Affected Users tab to see a list of all users that received the email.
Remediate: This action removes the email from all affected inboxes.
Mark as Safe: This action adds a green banner to this email marking it as safe. The email is restored to all affected inboxes.
Allow Sender: This action adds the sender to the Allow List. The email is delivered to the user's inbox without analysis. See Adding a Sender to the Allow List for additional information.
Allow Domain: This action adds the domain to the Allow List, so that any email using that domain is delivered to the user's inbox without analysis. See Adding a Domain to the Allow List for additional information.
Banners
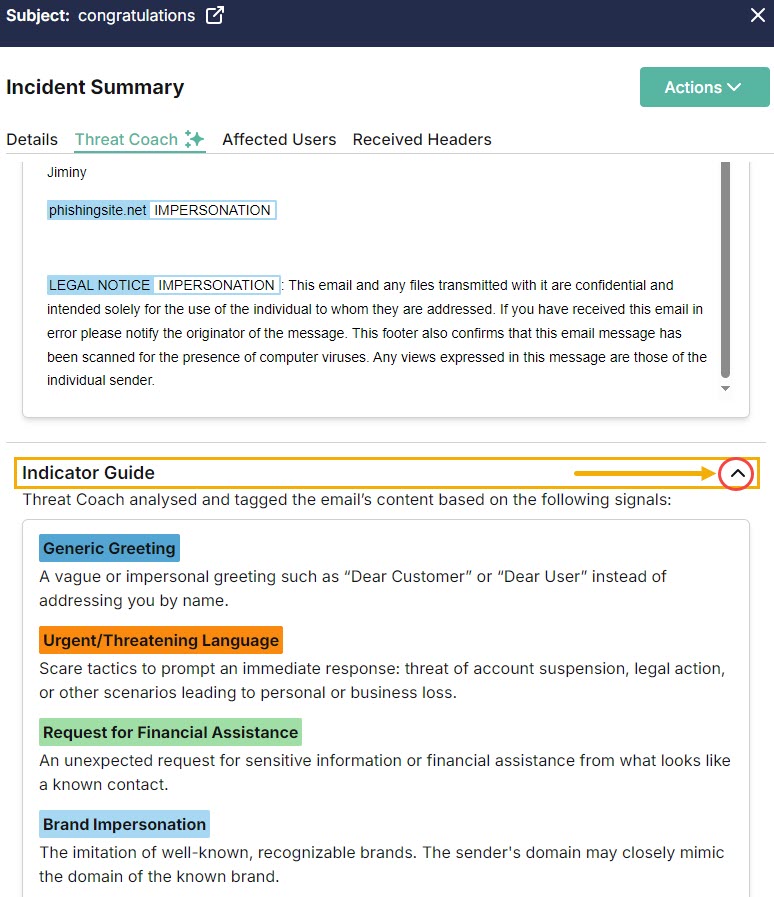
THREAT COACH
AFFECTED USERS
The date and subject of the email are listed here, along with the email addresses of the recipient and sender. The name of the customer is also listed.
RECEIVED HEADERS
The content of the received header is displayed.