Configuring SAML SSO
SAML (Security Assertion Markup Language) is a widely used solution that supports SSO (single sign-on). SAML SSO works by passing authentication information between your existing Identity Provider and the TitanHQ platform. This means your Identity Provider becomes the authentication method for accessing the platform, and you'll no longer need to use your username and password to log in.
To set up SAML SSO, you'll need to configure both your Identity Provider and your TitanHQ platform account. Make sure you're logged into both accounts before you begin.
Note
The instructions below use Microsoft Azure (Microsoft Entra ID) as the example Identity Provider. Your own Identity Provider may have different field names, however, the process is similar.
Azure is not owned or managed by TitanHQ, and as such, the information may be subject to change without us knowing. If you notice anything out of place, please email docs@titanhq.com and let us know.
In the TitanHQ platform, go to Settings > SAML SSO, and select the SAML SSO toggle to enable configuration.
When the SAML SSO configuration is enabled, the page is populated with a series of fields, which are explained below. In the steps that follow, you'll learn how to complete the fields.
Allow login with username & password
You can select this checkbox to allow you to use your username and password to log in. This is useful when you are initially setting up SAML SSO and get locked out due to configuration issues. It allows you to log in with your normal credentials instead.
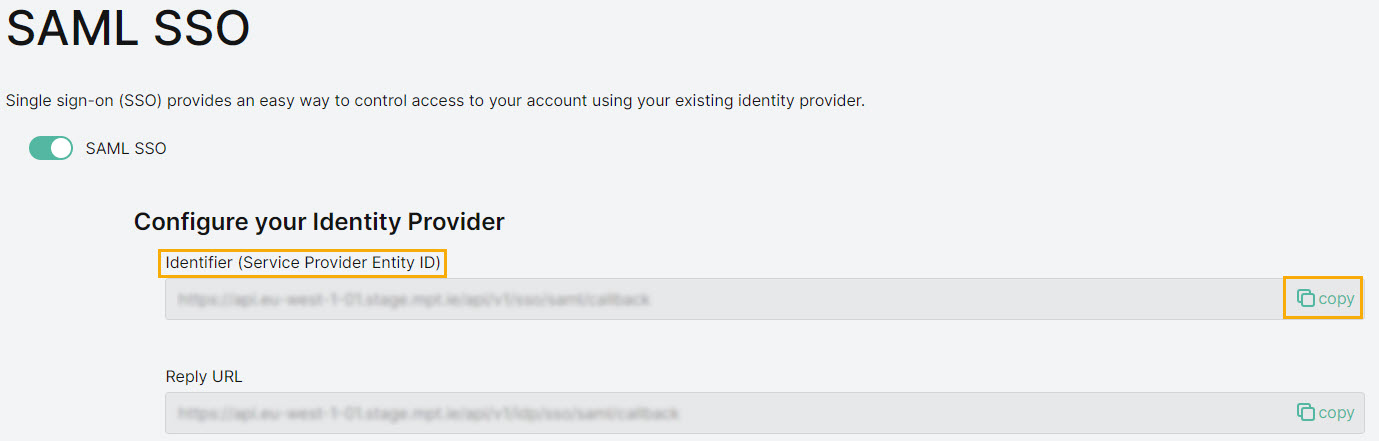
Configure your Identity Provider
Identifier (Service Provider Entity ID)
A unique ID that identifies the SAML SSO application to Microsoft Entra ID.
Reply URL
The location where the SAML SSO application receives the authentication token.
Setup SAML Authentication
Login URL
The URL address of your Identity Provider login location.
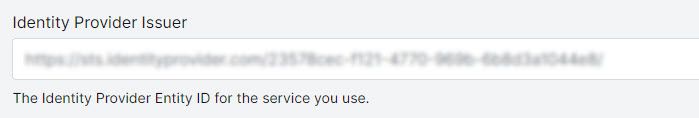
Identity Provider Issuer
The Identity Provider Entity ID for the service you use.
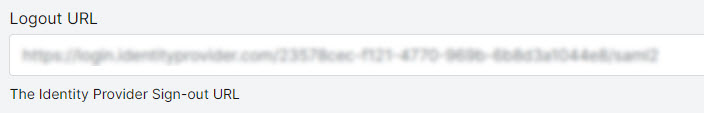
Logout URL
Your Identity Provider sign-out URL.
Public Certificate
A digital certificate that verifies secure communication between the Identity Provider and the platform.
Attributes for Claims
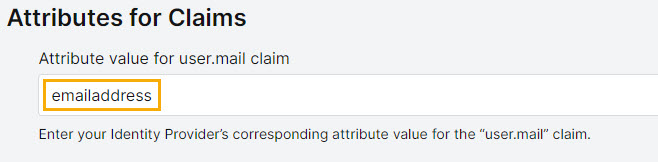
Attribute value for user.mail claim
Your Identity Provider’s corresponding attribute value for the user.mail claim.
Next, go to your Azure account, where you'll create a new application for SAML SSO.
Go to Enterprise applications and select New application.

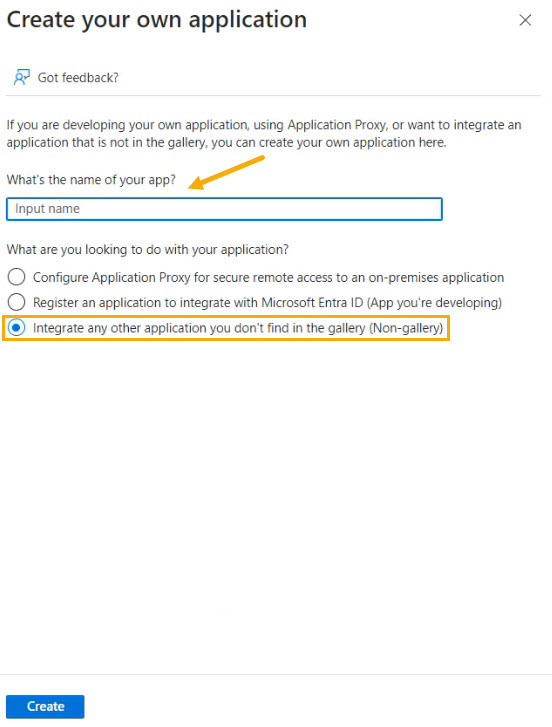
In the next window, select Create your own application.

Enter a name for your application, such as TitanHQ SAML SSO, and ensure Integrate any other application you don't find in the gallery (Non-gallery) is selected. Then select Create.
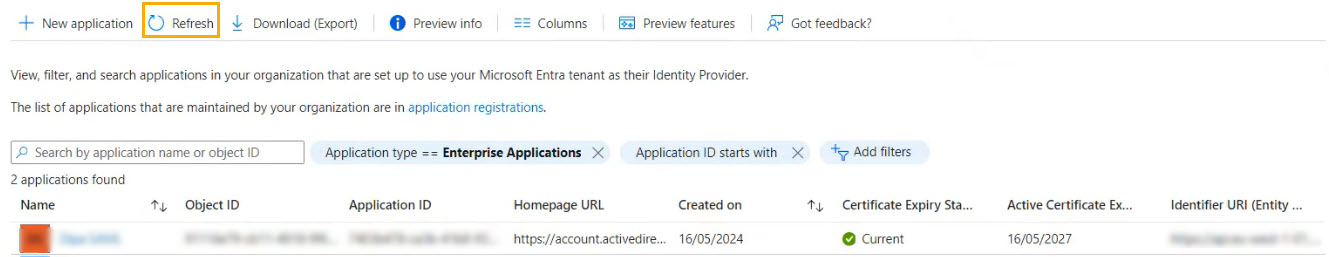
Once the new application is created, select Refresh to refresh your screen. The new app for SAML SSO will appear in your table of applications.
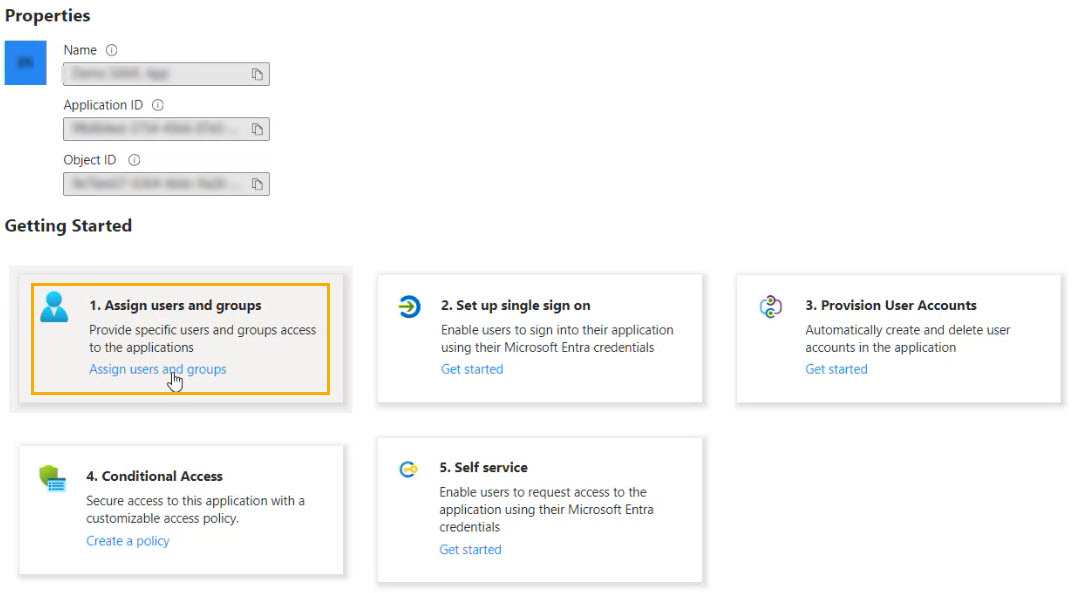
Next, you'll need to assign your email address to the app.
Select the app to open it and then select Assign users and groups.
Select Add user/group .
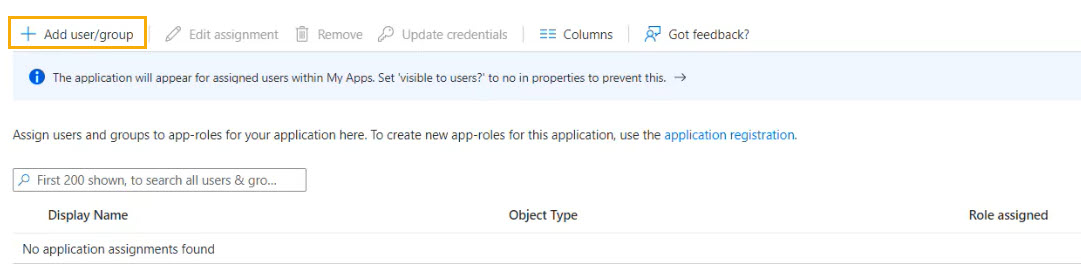
Select the link None Selected, and in the window that opens, select your admin address.
Once your email address is assigned to the SAML SSO app, you'll need to configure Azure with details from the platform.
Select the checkbox beside your Display Name, and then select Single sign-on in the left menu.
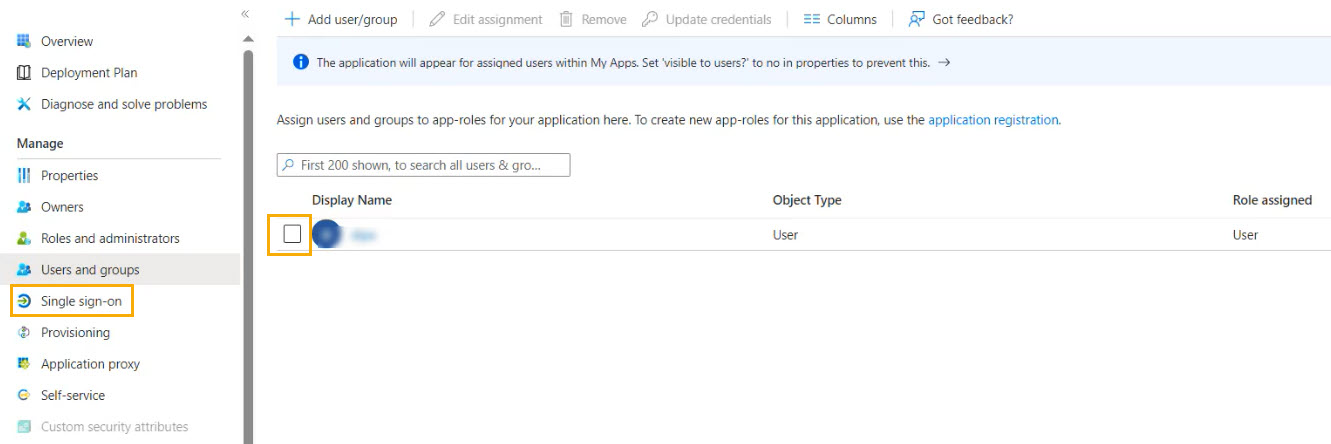
Select the single sign-on method SAML, which opens the Set up Single Sign-On with SAML window.
Go to the SAML SSO configuration page in the platform. In the Configure your identity Provider section, go to the Identifier (Service Provider Entity ID) field, and select Copy
 .
.
In Azure, select Edit in the Basic SAML Configuration section.
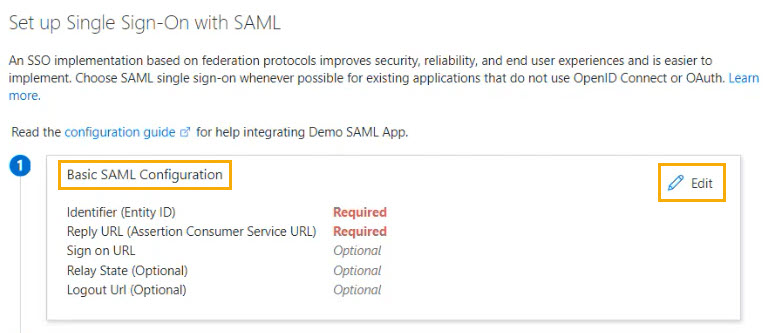
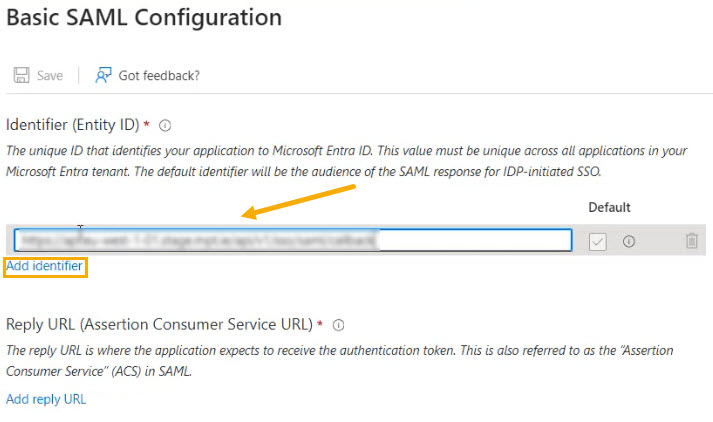
In the screen that opens, select Add Identifier, and in the Identifier (Entity ID) field, paste the contents from your Identifier (Service Provider Entity ID) field.
Next, you'll need to add the Reply URL. Go to the SAML SSO configuration page in the platform. In the Configure your identity Provider section, select Copy
 in the Reply URL field.
in the Reply URL field.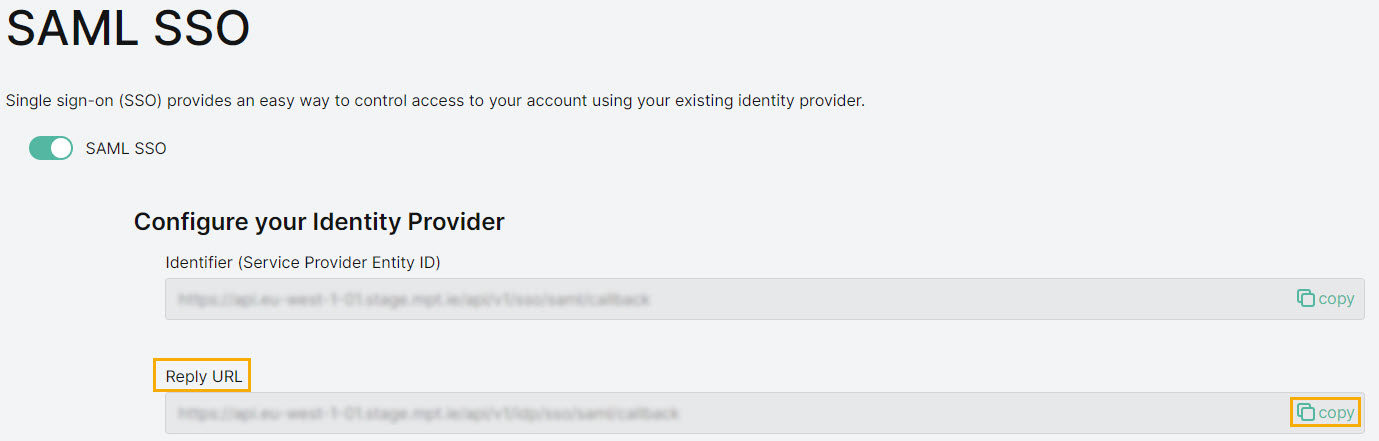
In Azure, select Add reply URL and paste the contents in the Reply URL (Assertion Consumer Service URL) field.
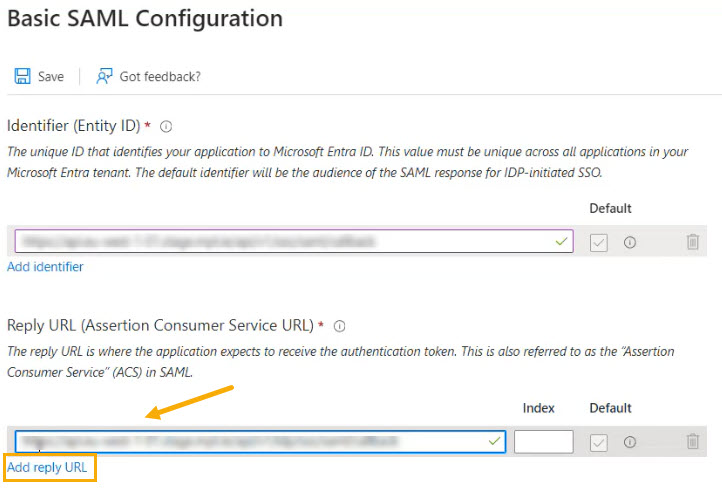
Once you've pasted details into the required fields, verify that the URLs appear in the Basic SAML Configuration section.
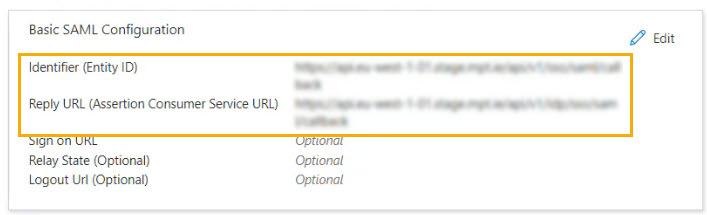
The updates required in Azure are now complete.
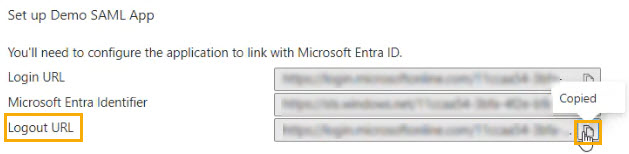
Next, you'll need to set up SAML authentication. This requires copying details from Azure to the SAML SSO configuration page in the platform. Begin by going to Azure, and locate the Set up Demo SAML App section.
In the Login URL field, select the copy
 icon.
icon.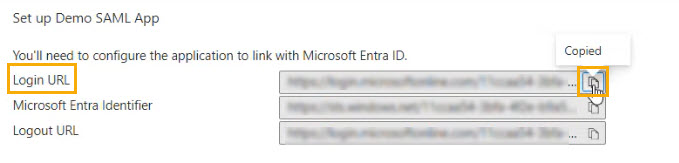
Go to the SAML SSO configuration page, and in the Setup SAML Authentication section, paste the contents in the Login URL field.
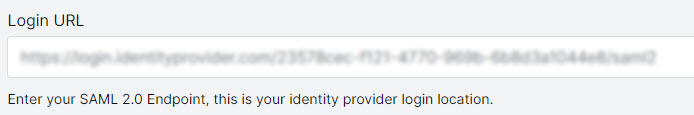
In Azure, copy the Microsoft Entra Identifier.
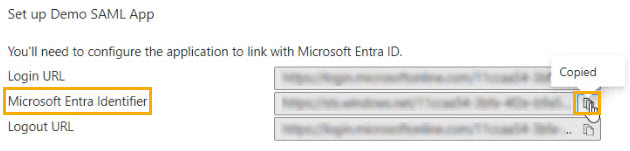
In the SAML SSO configuration page, paste the contents in the Identity Provider Issuer field.
Next, in Azure, copy the Logout URL.
In the SAML SSO configuration page, paste the contents in the Logout URL field.
In Azure, locate the SAML Certificates section, and select Download beside Certificate (Base64). Save it to your Downloads folder.
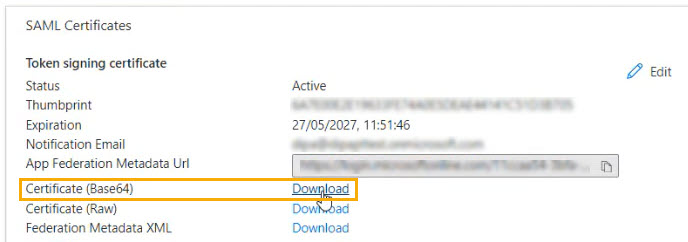
Open the file, copy the contents, and paste it in the Public Certificate field in the SAML SSO configuration page.
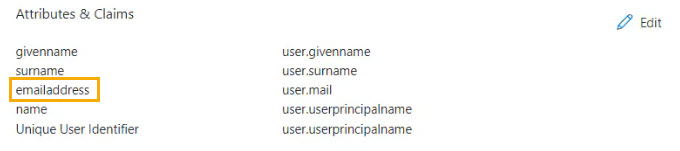
The last configuration item to update is the Attributes for Claims, which is the attribute required for the user.mail claim.
In Azure, go to the Attributes & Claims section, and copy emailaddress, which is the attribute for user.mail.
In the SAML SSO configuration page on the platform, paste emailaddress into the Attribute value for user.mail claim field.
Select Save. Once your configuration has been validated, a confirmation box appears, detailing the following three options:
Cancel: If you select Cancel, the configuration data you entered will not be saved and you'll be returned to the Configuration screen.
Save Config: If you select Save Config, the configuration data you entered will be saved, allowing you to enable SAML SSO later.
Enable: Selecting Enable means that your configuration data is saved, and SAML SSO login is now active.
Important
When you save and enable SAML SSO, if your current session expires, you must log in again using SAML SSO. You'll no longer be able to log in with a username and password. See Log in Using SAML SSO for details.