General Email Security Settings
In Email Security > General, you can set up the following:
Select an option for adding new identities: For new identities to be automatically added to EncryptTitan, an invitation needs to be issued. Select the identity who the invitation will be issued from. The list is now populated with identities who have a status of Active and Acceptance Required.
By default, this option is turned off. However, this is a mandatory step if you want users on the domain to be able to send emails for encryption, even when they have not completed their account setup or if they have not yet been added as an identity. See Editing Identities to learn how to set up a user as a service identity.
Note
If your spam filter has display name spoofing detection enabled, then it is recommended that you do not use a user alias for the service identity email address. This is because it may result in a display name false positive. It is recommended that a noreply, support, or admin alias be used, because these are unlikely to trigger a display name false positive.
If you have selected an identity and then decide you do not want identities automatically added to EncryptTitan and select OFF - Identities are not automatically added, you'll receive the following notification:
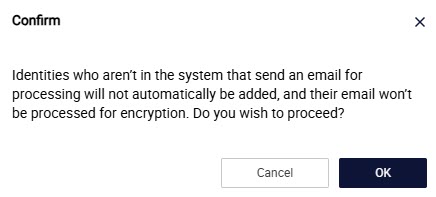
Retention policy (in days): Set the number of days for which the email will be retained. The default is 60 days.
Maximum file size allowed (in MB): Set the maximum file size that can be attached in the email.
Deliver replies from the Secure Portal directly to recipient’s Inbox: Enable this slider to allow email replies from the secure portal to be delivered directly to the identities inbox and not to the secure portal. When enabled, replies to emails from the secure portal will be delivered via Opportunistic TLS directly to the recipient's inbox. When disabled, replies from the secure portal to the emails of identities on this account are delivered to the secure portal. To view examples of how emails are delivered when this setting is enabled/disabled, see Appendix C: Use Cases for Replies from Secure Portal via Opportunistic TLS.